DDoS Mitigation
1Tbps+ Filterkapazität
DDoS Angriffe sind eine ständige Bedrohung. Sie gefährden die Verfügbarkeit Ihrer Infrastruktur und können Ihr Business ernsthaft schädigen. Ihr Zweck kann Erpressung, die Schädigung von Konkurrenten oder auch Vandalismus sein. Werden Sie nicht das nächste Opfer eines DDoS-Angriffs. Lassen Sie sich von unseren automatisierten, hocheffizienten und fachmännisch entwickelten DDoS-Mitigation-Services schützen.

Wie funktioniert unser DDoS Schutz?
Sobald ein Subnet für den DDoS Schutz aktiviert wurde, können pro IP folgende Modi gesetzt werden:
- „Sensor Mode“ – Erkennt und startet die DDoS-Mitigation für den Datenverkehr nur, wenn ein DDoS-Angriff erkannt wird
- „always on“ – Der Datenverkehr wird durchgehend nach DDoS-Angriffen gefiltert. Dies ist sinnvoll für IPs, die sehr empfindlich auf plötzlichen Traffic reagieren. Wir empfehlen diesen Status jedoch nur, wenn dies erforderlich ist
- „always off“ – Keine Erkennung/Filterung aktiviert
Für die ersten beiden Zustände haben Sie die Möglichkeit, die Filterung von Layer 7 zu deaktivieren (die standardmäßig aktiviert ist).
Wir inspizieren die Layer 2, 3, 4 und 7, bei denen es sich eigentlich um alle Schichten handelt, die für die Inspektion relevant sind.
Wenn Sie unseren Anti-DDoS-Filter mit Layer-7-Filterung (Reverse-Proxy) verwenden, wird der Inhalt Ihrer Site bei einem Angriff auf den Webserver-Port 80 vom DDoS-Filter zwischengespeichert.
Wie funktioniert der „Sensor Mode“?
Wenn kein Angriff auf Ihre IP-Adresse erfolgt, fließt der Datenverkehr, wie im normalen Betriebsmodus, direkt zu Ihrem Gerät:
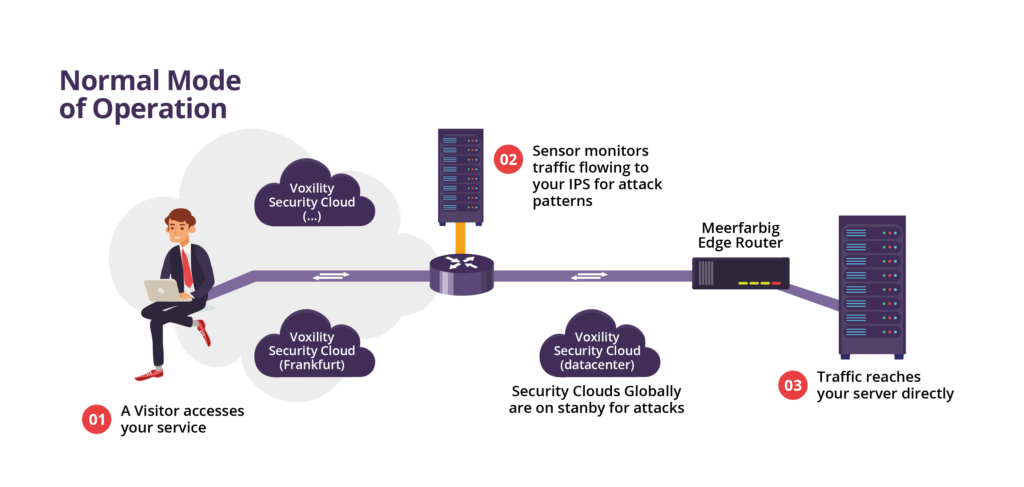
Voxility verfügt über Sensoren, um Angriffe überall im Netzwerk zu erkennen. Wenn ein verdächtiges Muster erkannt wird, wird der Verkehr zu einer Sicherheitscenter-Cloud umgeleitet.
Die Netzwerksensoren erkennen sofort, wenn ein Angriff auftritt, und leiten den Datenverkehr in Sekunden von der betroffenen IP-Adresse zur Mitigations-Cloud um:
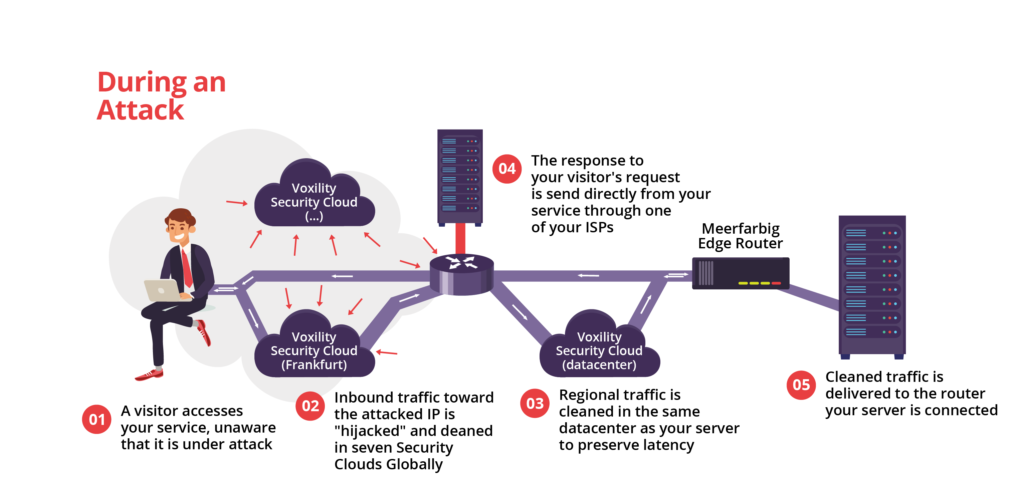
Die Umleitung stoppt innerhalb von Minuten nach dem Ende des Angriffs.
Wie funktioniert der „always on“ Mode?
Anstatt zuzulassen, dass Datenverkehr direkt zu Ihrem Server geleitet wird, wendet dieser Schutzmodus permanent die Anti-DDoS-Filter an. Grundsätzlich fließt der Verkehr permanent durch die Voxility Security Cloud.
Wie kann ich die Anti-DDoS Mitigation buchen?
Aktuell gibt es mehrere Möglichkeiten, den DDoS-Schutz zu beziehen:
- Sie haben einen Server bei meerfarbig? Kontaktieren Sie uns einfach bzgl. der Preisstruktur. Der Schutz kann innerhalb kürzester Zeit aktiviert werden. Bei einem laufenden Angriff auf Ihre Infrastruktur sind wir 24/7 behilflich diesen schnellstmöglich zu mitigieren.
- Sie betreiben Ihr eigenes Netzwerk/ASN? Gerne bieten wir Ihnen eine white-labeled BGP Session an. Sie announcen ein more Specific über unsere Session woraufhin der Schutz greift. Aktuell können wir Ihnen in den meisten Frankfurter Datacentern einen Anschluss anbieten. Kontaktieren Sie uns gerne für Ihr persönliches Angebot.
